
Madsonic supports authentication with LDAP, group mapping and more ...
This guide assumes that you have successfully installed the Madsonic server on your computer.
If not, please refer to the installation instructions.
After installing and starting Madsonic, open the Madsonic web page.
The web address may differ depending on your installation options, but is typically
http://localhost:4040.
You must have a online access to your LDAP server and credential to join communication.
you can use this group terms for LDAP autoMapping.
madsonic.admin --> Madsonic administrator role
madsonic.config --> Madsonic change settings role
madsonic.stream --> Madsonic can play media role
madsonic.search --> Madsonic search role
madsonic.cover --> Madsonic cover & comment edit role
madsonic.upload --> Madsonic can upload role
madsonic.jukebox --> Madsonic jukebox user role
madsonic.download --> Madsonic download role
madsonic.podcast --> Madsonic podcast administrator role
madsonic.comment --> Madsonic editor role
madsonic.lastfm --> Madsonic last.fm usage role
madsonic.share --> Madsonic share role
madsonic.image --> Madsonic image role (reserved)
madsonic.video --> Madsonic video role (reserved)
madsonic.audioconversion --> Madsonic audio conversion role (updated with Madsonic 6.3)
madsonic.videoconversion --> Madsonic video conversion role (updated with Madsonic 6.3)
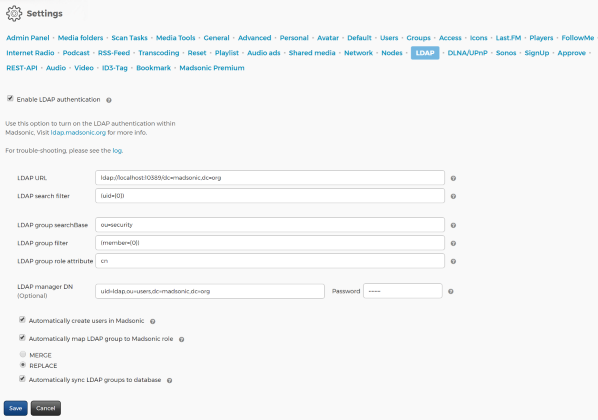
Madsonic LDAP config template
LDAP URL: ldap://localhost:389/dc=madsonic,dc=org
LDAP search filter: (sAMAccountName={0})
LDAP group searchBase: ou=groups,ou=organisation
LDAP group filter: (member={0})
LDAP group role attribute: cn
LDAP manager DN: cn=ldap,ou=users,ou=organisation,dc=madsonic,dc=org
LDAP manager password: the given password
Madsonic LDAP config template
LDAP URL: ldap://localhost:10389/dc=madsonic,dc=org
LDAP search filter: (uid={0})
LDAP group searchBase: ou=groups
LDAP group filter: (member={0})
LDAP group role attribute: ou
LDAP manager DN: uid=ldap,ou=users,dc=madsonic,dc=org
LDAP manager password: the given password
Madsonic LDAP config template
LDAP URL: ldap://localhost:389/dc=madsonic,dc=org
LDAP search filter: (uid={0})
LDAP group searchBase: ou=groups
LDAP group filter: (member={0})
LDAP group role attribute: cn
LDAP manager DN: cn=ldap,ou=users,dc=madsonic,dc=org
LDAP manager password: the given password
Activate Automatically map LDAP group and set mode to REPLACE
Activate Automatically sync LDAP group to allow the withdrawn roles to be removed from the local user.
Example:
User Bob is member of madsonic.admin and madsonic.stream
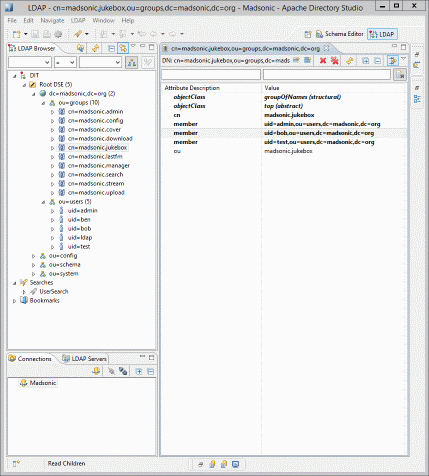
dn: ou=groups,dc=madsonic,dc=org objectClass: top objectClass: organizationalUnit ou: groups dn: ou=users,dc=madsonic,dc=org objectClass: top objectClass: organizationalUnit ou: users dn: uid=bob,ou=users,dc=madsonic,dc=org objectclass: top objectclass: inetOrgPerson objectclass: person objectclass: organizationalPerson cn: bob sn: bob uid: bob displayName: bobuser userPassword: bob dn: cn=madsonic.stream,ou=groups,dc=madsonic,dc=org objectClass: groupOfNames objectClass: top cn: madsonic.stream ou: madsonic.stream member: uid=bob,ou=users,dc=madsonic,dc=org dn: cn=madsonic.admin,ou=groups,dc=madsonic,dc=org objectClass: groupOfNames objectClass: top cn: madsonic.admin ou: madsonic.admin member: uid=bob,ou=users,dc=madsonic,dc=org
For trouble-shooting go to Settings > Admin Panel > Logfile Logging level
Set output to DEBUG or VERBOSE for detailed info in the log file.
See advanced LDAP verbose output with Madsonic Build >= 6.3.9720
[10/17/17 10:01 AM] DEBUG MadsonicContextSource URL 'ldap://10.0.0.7:389/dc=madsonic,dc=org', root DN is 'dc=madsonic,dc=org'
[10/17/17 10:01 AM] DEBUG MadsonicLdapBindAuthenticator create LDAP delegation for user bob
[10/17/17 10:01 AM] DEBUG MadsonicLdapBindAuthenticator user 'bob' successfully authenticated in LDAP. DN: uid=bob,ou=users
[10/17/17 10:01 AM] DEBUG SecurityService Cloned from default user: bob
[10/17/17 10:01 AM] INFO MadsonicLdapBindAuthenticator cloned from default user 'bob' for DN uid=bob,ou=users
[10/17/17 10:01 AM] DEBUG SecurityService Updated user default
[10/17/17 10:01 AM] DEBUG MadsonicLdapBindAuthenticator set token for bob
[10/17/17 10:01 AM] DEBUG MadsonicContextSource URL 'ldap://10.0.0.7:389/dc=madsonic,dc=org', root DN is 'dc=madsonic,dc=org'
[10/17/17 10:01 AM] VERBOSE MadsonicLdapAuthoritiesPopulator Getting authorities for user uid=bob,ou=users,dc=madsonic,dc=org
[10/17/17 10:01 AM] VERBOSE MadsonicLdapAuthoritiesPopulator Searching for roles for user 'bob', DN = 'uid=bob,ou=users,dc=madsonic,dc=org', with filter (member={0}) in search base 'ou=security'
[10/17/17 10:01 AM] VERBOSE MadsonicLdapAuthoritiesPopulator Roles from search: [madsonic.stream]
[10/17/17 10:01 AM] VERBOSE UserDetailsServiceBasedAuthoritiesPopulator DB: []
[10/17/17 10:01 AM] VERBOSE UserDetailsServiceBasedAuthoritiesPopulator LDAP: [ROLE_MADSONIC.STREAM]
[10/17/17 10:01 AM] VERBOSE UserDetailsServiceBasedAuthoritiesPopulator retrieved roles: [ROLE_STREAM]
[10/17/17 10:01 AM] DEBUG UserDetailsServiceBasedAuthoritiesPopulator Successfully synced roles to DB.
[10/17/17 10:01 AM] INFO PlayerDao Created player 26.
[10/17/17 10:01 AM] DEBUG PlayerService Created player 26 (remoteControlEnabled: true, isStreamRequest: false, username: bob, ip: 127.0.0.1).